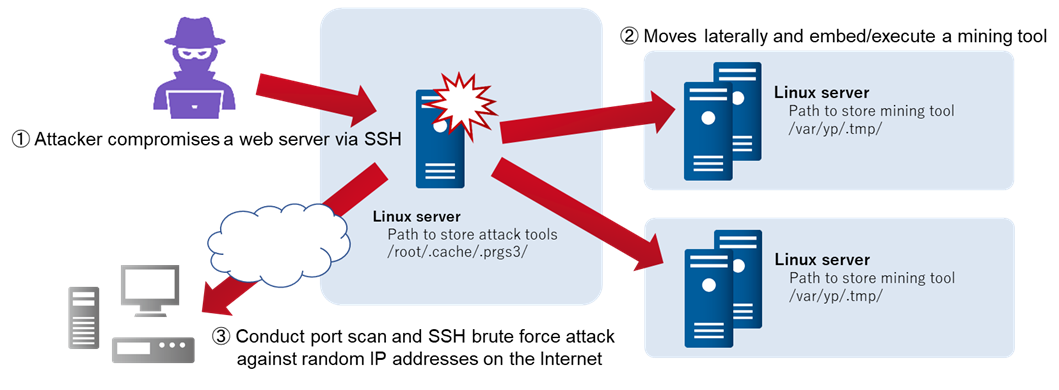
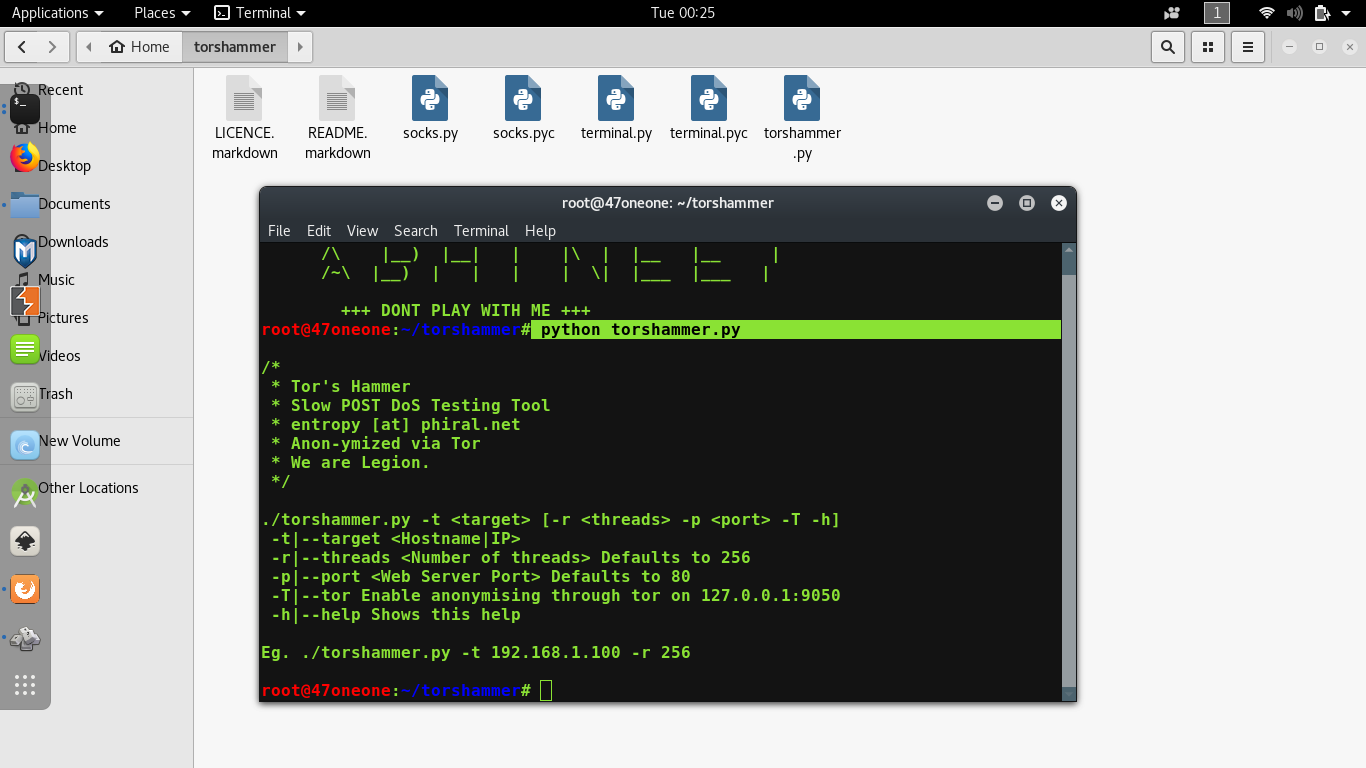
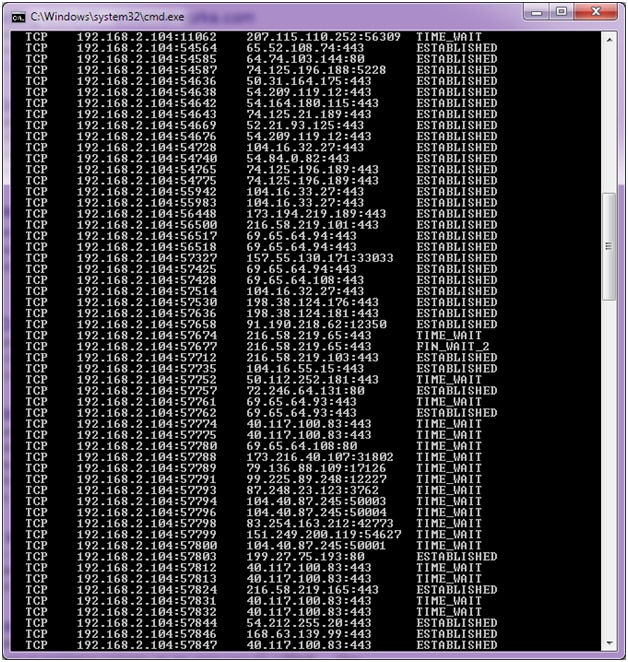
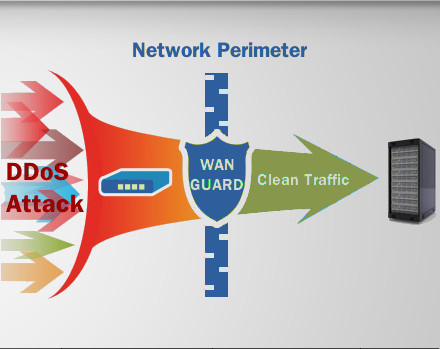
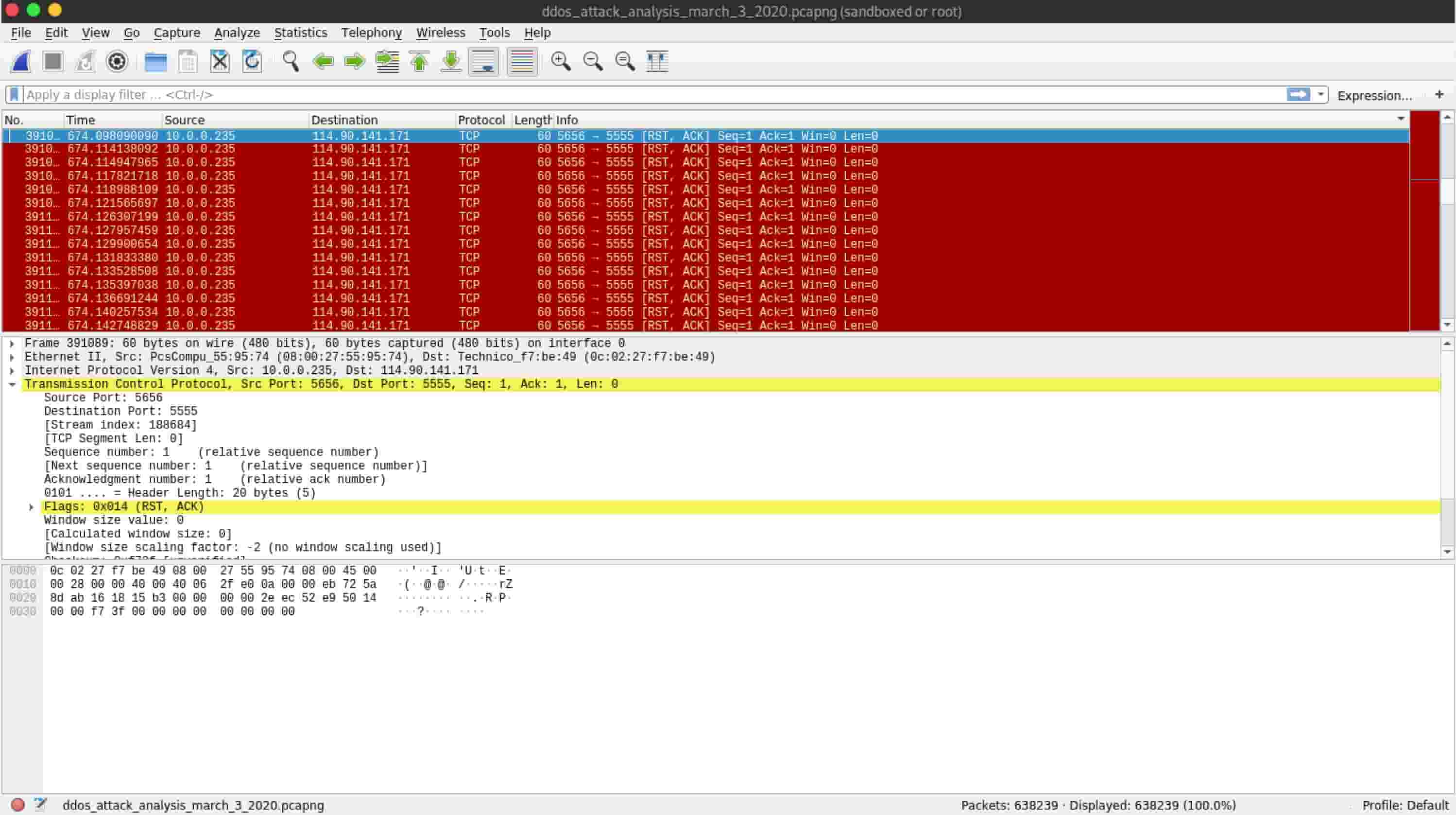
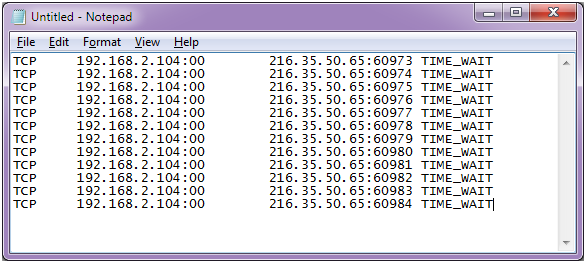
How to quickly check to see if your Linux server is under a DoS attack from a single IP address – Nasni Consultants

Classification of DDoS Attacks VI. DISCUSSION Preventing DDoS attacks... | Download Scientific Diagram
A simplified model of a botnet conducting a DDoS attack. Once an army... | Download Scientific Diagram
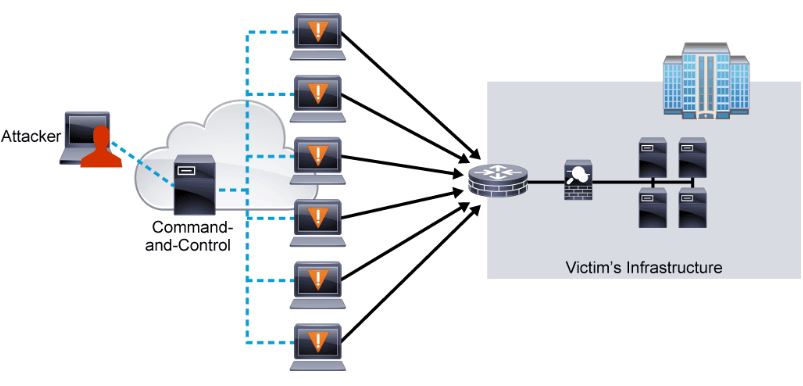
DoS and DDoS attack-The Ultimate goal for CCNA, Cisco Networking, Cisco Certification Exam, Linux Installation and Server Management

2017 DDoS and Web Application Attack Landscape - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.